After everything you’ve invested in building your platform, the last thing you need is a payment processing partner that slows you down. For integrated software vendors (ISVs), payments aren’t just another feature or add-on. Your payment processor becomes a direct extension of your product, your brand, and the experience you …
February, 2026
-
18 February
Bluefin Links to Basis Theory and other Digital Transactions News briefs from 2/18/26
Bluefin has partnered with Basis Theory, a tokenization and vaulting platform, to allow sensitive payment data to be captured, tokenized, and used across channels. The two companies say they will implement a unified token strategy across in-store, call center, online, and backend payment environments without expanding PCI scope or introducing new …
-
17 February
Airbnb Expands Reserve Now, Pay Later Globally
Airbnb Inc. has expanded its Reserve Now, Pay Later booking option worldwide. The service enables travelers to reserve properties and rooms without an upfront payment to reserve the space. Full payment is due prior to the closing of the free cancellation window, which is set by the property owner. The …
-
17 February
A Global Survey Uncovers a Strong Following for Stablecoins
Research released early Tuesday argues stablecoins have made their move out of niche applications and into the mainstream of international payments, propelled by fast transactions and perceived security. That’s according to the “Stablecoin Utility Report” from stablecoin-technology provider BVNK, with research conducted by YouGov among more than 4,600 digital-currency users …
-
17 February
Can/Am’s Teller Payments and other Digital Transactions News briefs from 2/17/26
Can/Am Technologies Inc. has introduced Teller Payments, aimed at helping state, local, and education agencies process payments within Can/Am’s Teller Government Cashiering system. The processor Fiserv Inc. is supporting the service through its independent software vendor partner program. Metropolitan Commercial Bank, based in New York City, is one of the first …
-
16 February
Japanese Fintech PayPay Looks to Enter the U.S. Via a Visa Partnership And an IPO
Japanese fintech PayPay Corp. is preparing a push into the United States through a partnership with Visa Inc. and an initial public offering. Through Visa, PayPay will develop new payment options for its mobile wallet beyond QR codes to broaden its wallet appeal to U.S. consumers. PayPay specializes in QR …
-
16 February
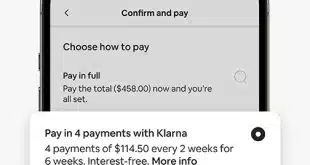
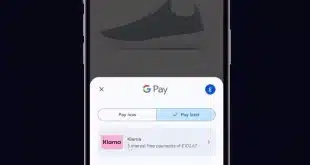
A Rapidly Growing Klarna Joins Google Pay in the U.K.
Klarna AB announced early Monday its pay-over-time service has become an available payment option in Google Pay in the United Kingdom, joining a list of payment services already operating through the wallet. The move represents a major geographic expansion of previous actions by the two companies. Last year, Google Pay …
-
16 February
Hoot Host’s Launch and other Digital Transactions News briefs from 2/16/26
Hoot Host launched an expanded version of its software-with-a-service product for online businesses, including payments acceptance through PayPal, Square, and Stripe. The cryptocurrency exchange OKX, based in the Seychelles and with a regional headquarters in San Jose, Calif., received a Payment Institution license in Malta, a move that will allow the company …